Using Message Security with Java EE
in the document, the use of XML Encryption and XML Digital Signature to
secure SOAP messages and attachments is strongly recommended by this orga-
nization. Using Message Security with Java EE (page 241) discusses some
options for securing messages with Java EE.
message security is a very important component of web services security, this
section presents a brief introduction to using both the Application Server's Web
Services Security (WSS) and the Java WSDP's XML and Web Services Security
(XWSS) functionality.
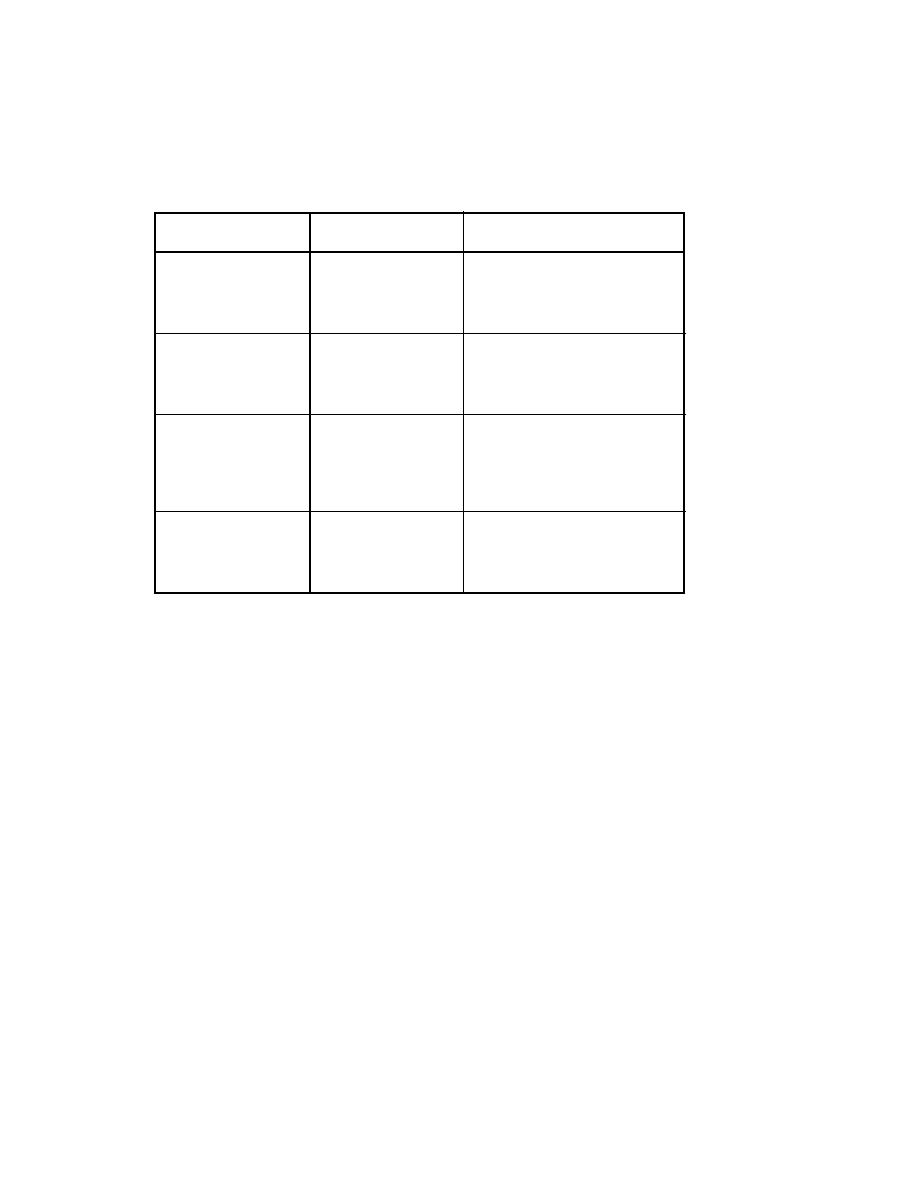
tion and Authentication
in the middle, principal
spoofing, forged claims,
replay of message parts
-MIME with XML Signature/XML
Encryption
-XML Signature
ing Transport Data Integ-
rity and SOAP Message
Integrity)
replay
-XML Signatures (as profiled in
OASIS SOAP Message Security)
(including Transport
Data Confidentiality and
SOAP Message Confi-
dentiality)
-XML Signatures (as profiled in
OASIS SOAP Message Security)
replay, denial of service
generated the request and the node
that is guaranteeing
-Signing of nonce, time stamp