Security Challenges and Threats
and the User Name and X.509 security token formats.
Expression Language (REL) security token that is used with WS-Secu-
rity.
guage (SAML) security token that is used with WS-Security.
web service application, and identifies appropriate candidate technologies
to address these challenges. The section Security Challenges, Threats, and
Countermeasures (page 240) discusses the challenges, threats, and coun-
termeasures in a bit more detail.
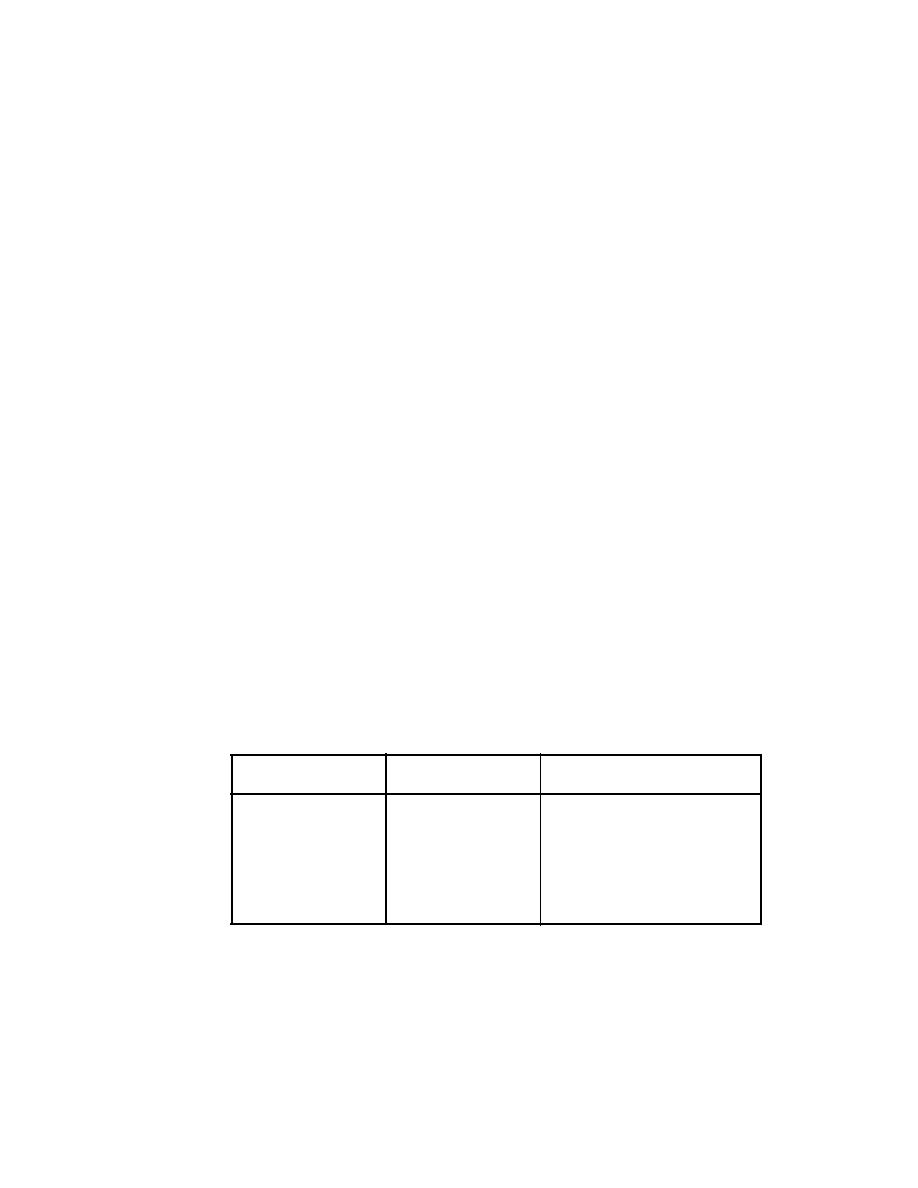
Countermeasures
can be read in its entirety at
Authentication
in the middle, principal
spoofing, forged claims,
replay of message parts
cation
-HTTP client authentication (Basic
or Digest)
-HTTPS with X.509 mutual authenti-
cation of server and user agent
-OASIS SOAP Message Security