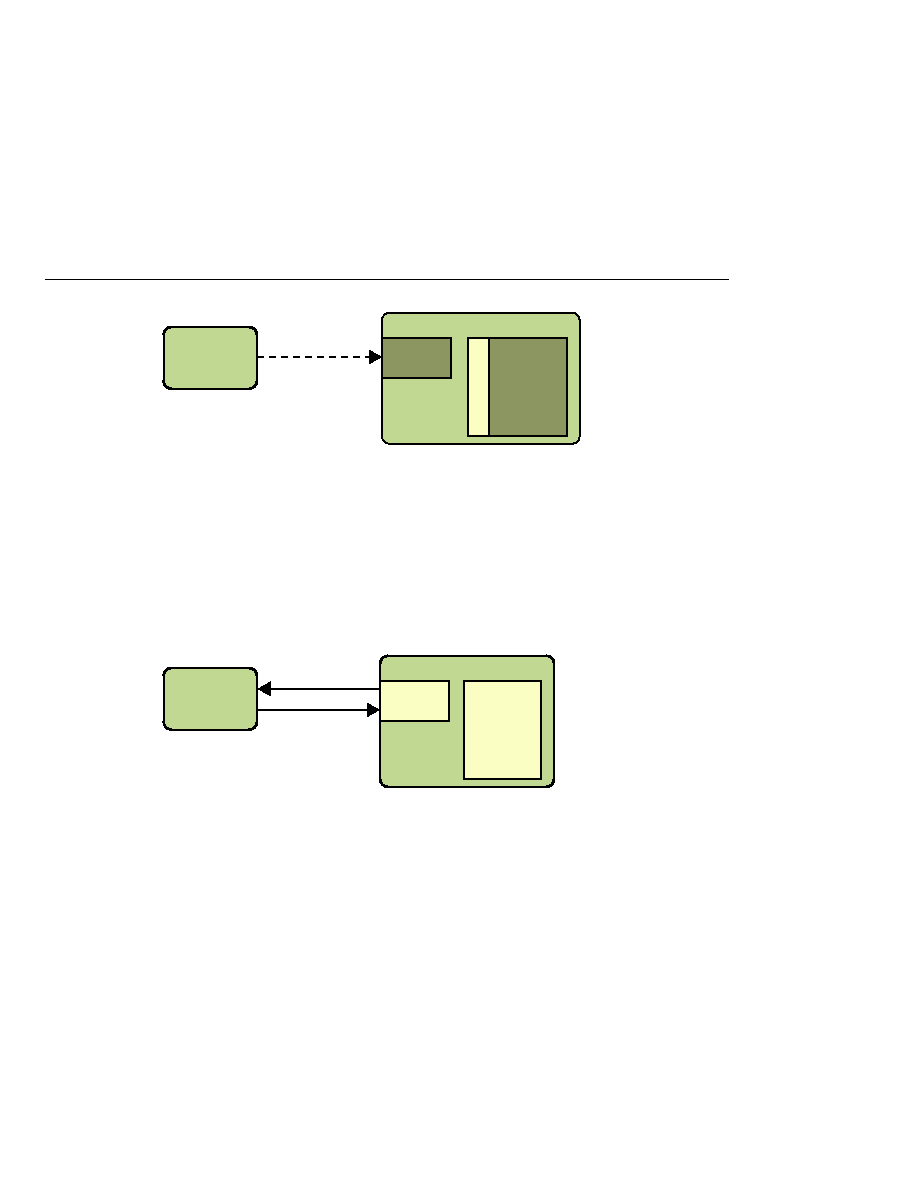
Fulfilling the Original Request
Fulfilling the Original Request
The web server's evaluation stops with an "is authorized" outcome when the web server is able
to map the user to a role. A "not authorized" outcome is reached if the web server is unable to
map the user to any of the permitted roles.
Step 4: Fulfilling the Original Request
If the user is authorized, the web server returns the result of the original URL request, as shown
in
In our example, the response URL of a JSP page is returned, enabling the user to post form data
that needs to be handled by the business logic component of the application. Read
for more information on protecting web applications.
Step 5: Invoking Enterprise Bean Business Methods
The JSP page performs the remote method call to the enterprise bean, using the user's credential
to establish a secure association between the JSP page and the enterprise bean (as shown in
). The association is implemented as two related security contexts, one in the web
server and one in the EJB container.
Web Client
Web Server
credential
JSP/servlet
Object
Request access
to protected
resource
Session
Context
A
uthor
ization
FIGURE 283
URL Authorization
Web Client
Result
of request
Post to
business logic
Web Server
credential
JSP/servlet
Session
Context
FIGURE 284
Fulfilling the Original Request
Overview of Java EE Security
The Java EE 5 Tutorial · September 2007
768
